Sep 16, 2024
sysbraykr.com news - Researchers at Cado Security Labs have uncovered two malicious campaigns that exploit misconfigured instances of Selenium Grid. Once a trusted tool for browser automation and testing, Selenium Grid has now become a target for cybercriminals, who are deploying exploit kits, cryptominers, and proxyjackers through its vulnerabilities.
Selenium Grid is a widely used, open-source platform designed to run automated test cases across different browsers and versions in parallel. Embraced by millions of developers worldwide, including those at major enterprises, startups, and open-source projects, Selenium Grid is a vital part of the continuous integration/continuous delivery (CI/CD) pipeline for testing web applications.
However, its default configuration lacks built-in authentication, making it an easy target for attackers. Cybercriminals have found a way to leverage this oversight, turning Selenium Grid into a tool for nefarious activities.
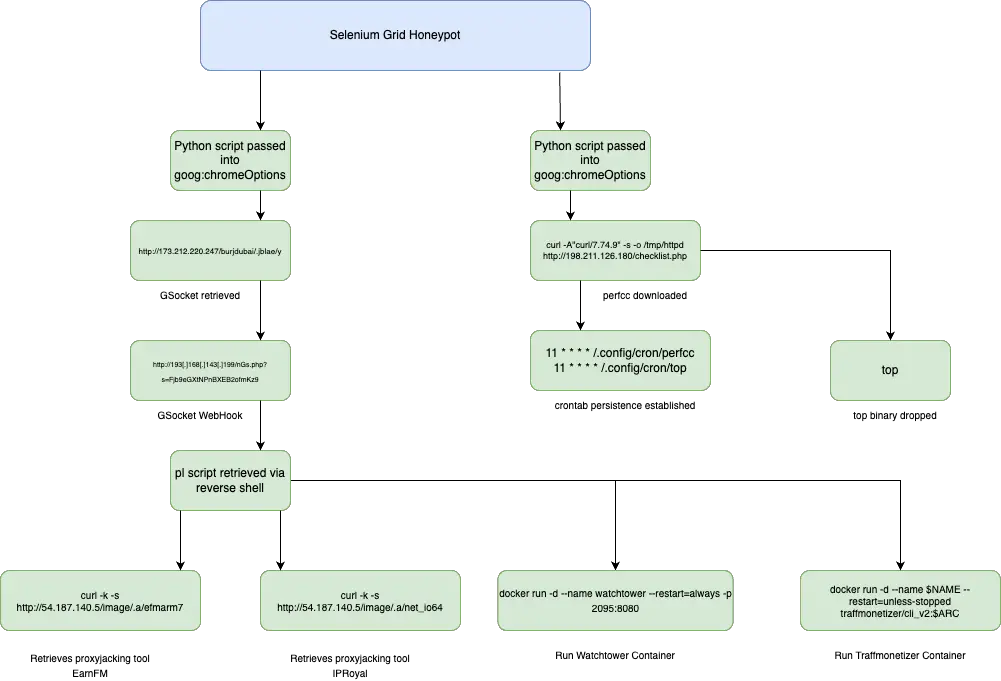
Attack Flow of Each Campaign | Image: Cado Security Labs
Cado Security Labs’ findings come on the heels of an earlier discovery made by researchers at Wiz, who identified a cryptomining campaign named SeleniumGreed. This campaign took advantage of the misconfiguration in Selenium Grid to hijack resources for cryptomining purposes. The new campaigns discovered by Cado Security Labs build on these tactics, exploiting similar vulnerabilities for both cryptomining and proxyjacking.
Cado Security’s honeypot network detected two distinct campaigns targeting Selenium Grid. In the first attack, the threat actors injected a base64 encoded Python script via the “goog:chromeOptions” configuration. This malicious script bypassed logging mechanisms, downloaded a reverse shell script from a remote server, and executed it without leaving traces.
The second campaign followed a similar attack pattern, injecting another base64 encoded Python script, which in turn downloaded and executed an ELF binary. This binary attempted to exploit an older vulnerability (CVE-2021-4043, commonly known as PwnKit) to escalate privileges to root. Once it gained elevated access, the binary downloaded and deployed the “perfcc” cryptominer, turning the victim’s machine into a cryptomining node.
One of the most concerning aspects of these campaigns is the rise of proxyjacking—a form of exploitation where an attacker hijacks a victim’s internet connection and sells their bandwidth as a residential proxy for profit. In one instance, the attackers downloaded IPRoyal Pawns and EarnFM payloads, allowing them to turn the victim’s internet connection into a proxy server that could be sold on the black market.
These proxyjacking payloads were designed to blend seamlessly into the system, running stealthily in the background. The attackers made extensive use of legitimate proxy tools, such as IPRoyal, to monetize compromised systems without raising suspicion.
The attackers’ methods were highly sophisticated, involving system architecture checks, privilege escalations, and the use of encrypted networking tools like GSocket for command and control (C2) communication. By using tools like UPX to pack the malware binaries, the attackers made detection and analysis difficult. Their scripts even removed temporary files and disabled logging, making it harder for forensic investigators to trace their activities.
The exploitation also extended to Docker environments, where the attackers stopped legitimate containers, such as WatchTower and Traffmonetizer, and replaced them with their own malicious instances.
Cryptomining and proxyjacking campaigns like these drain valuable resources, compromise security, and degrade system performance. For organizations that rely on Selenium Grid for CI/CD pipelines, the impact could be devastating, leading to financial loss, data theft, and system downtime.





