Sep 23, 2024
sysbraykr.com news - Here at Kaspersky Daily we’re forever urging readers of our blog to be real careful when downloading content to their devices. After all, even Google Play isn’t immune to malware — let alone unofficial sources with mods and hacked versions. For as long as the digital world keeps turning, Trojans will continue to worm their way onto devices that don’t have reliable protection.
Today we tell the story of how 11 million Android users worldwide fell victim to the Necro Trojan. Read on to learn which apps we found it in — and how to protect yourself.
What is Necro
Our regular readers may recall reading about Necro when we first wrote about it back in 2019. Back then, our experts discovered a Trojan in CamScanner, a text recognition app, which had clocked up over 100 million downloads on Google Play. Now the “necromancers” have injected new blood into the old Trojan: we found a version richer in features both in popular apps on Google Play and in various app mods on unofficial sites. Most likely, the developers of these apps used an unverified ad integration tool through which Necro infiltrated the code.
Today’s Necro is a loader obfuscated to avoid detection (but that didn’t stop us from finding it). It downloads the malicious payload in no less a crafty way using steganography to hide its code in a seemingly harmless image.
And downloaded malicious modules are able to load and run any DEX files (compiled code written for Android), install downloaded apps, tunnel through the victim’s device, and even — potentially — take out paid subscriptions. In addition, they can display and interact with ads in invisible windows, as well as open arbitrary links and run any JavaScript code.
Read more about how Necro is designed and how it operates on our Securelist blog.
Where Necro hides
We found traces of the malware in a user-modded version of Spotify, in the photo editing app Wuta Camera, in Max Browser, and in mods for both WhatsApp and popular games (including Minecraft).
In modded Spotify
At the very start of our investigation, our eye was caught by an unusual modification of the Spotify Plus app. Users were invited to download a new version of their favorite app from an unofficial source — for free and with an unlocked subscription offering unlimited listening, both online and off. The nice green Download Spotify MOD APK button looks so tempting, right? Stop! It’s malware. Never mind the Security Verified and Official Certification guarantees; this app will wreak havoc.

Well I never, all versions are viewable. Could Necro or other Trojans be lurking there too?
When this app was launched, the Trojan sent information about the infected device to the attackers’ C2 server, and in response got a link to download a PNG image. The malicious payload was hidden in this image by means of steganography.
In apps on Google Play
While the Spotify mod was distributed through unofficial channels, the Necro-infected Wuta Camera found its way onto Google Play, from where the app was downloaded more than 10 million times. According to our data, the Necro loader penetrated version 6.3.2.148 of Wuta Camera, with clean versions starting from 6.3.7.138. So, if your version is lower than that, you need to update immediately.
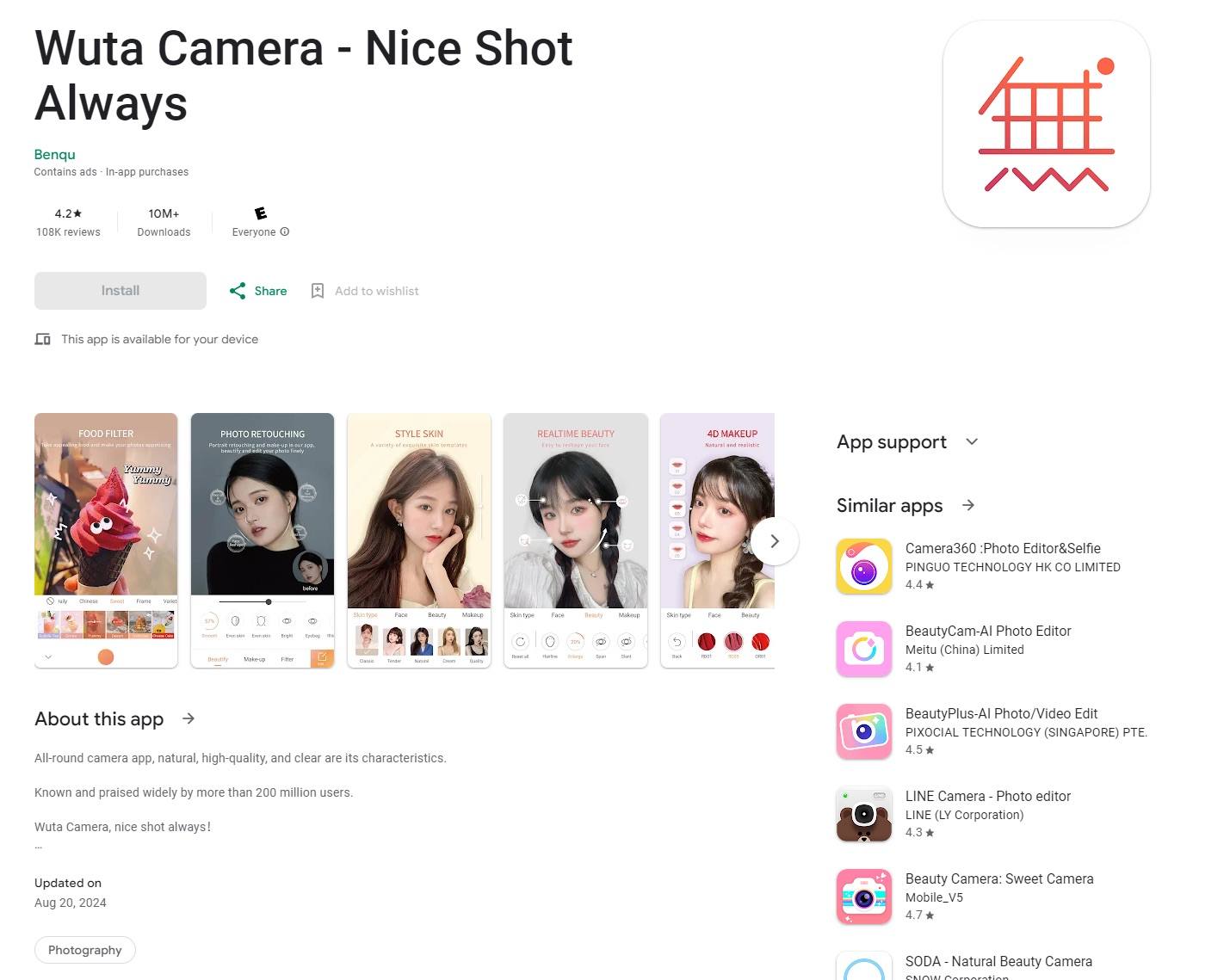
The impressive download count and decent ratings masked a Trojan
Max Browser’s audience is much smaller — just one million users. Necro infiltrated its app code in version 1.2.0. The app was removed from Google Play following our notification, but it’s still available on third-party resources. These, of course, should be trusted even less, since trojanized versions of the browser may still live there.
In mods for WhatsApp, Minecraft, and other popular apps
Alternative messenger clients usually boast more features than their official cousins. But you should treat all mods, be they on Google Play or a third-party site, as suspicious, for they often come bundled with Trojans.
For instance, we found mods for WhatsApp with the Necro loader being distributed from unofficial sources, as well as mods for Minecraft, Stumble Guys, Car Parking Multiplayer, and Melon Sandbox. And this selection sure isn’t random — attackers always target the most popular games and apps.
How to guard against Necro
First of all, we strongly advise against downloading apps from unofficial sources because the risk of device infection is extremely high. Secondly, apps on Google Play and other official platforms should also be treated with a healthy dose of skepticism. Even a popular app like Wuta Camera, with 10 million downloads, proved powerless in the face of Necro.
Make sure to protect your devices so as not to be caught off guard by a Trojan. Kaspersky for Android detects Necro and other similar malware.
Check the app page in the store before downloading. We particularly recommend looking at reviews with low ratings, as these generally give heads-up about potential pitfalls. Rave reviews could be fake, while a high overall score is easy to inflate.
Don’t look for mods or hacked versions. Such apps are almost always stuffed with all kinds of Trojans: from the most harmless to mobile spyware like CanesSpy.
source : https://www.kaspersky.com/blog/necro-infects-android-users/52201/





