Setiap Perusahaan Membutuhkan





HAAS
HAAS
HAAS
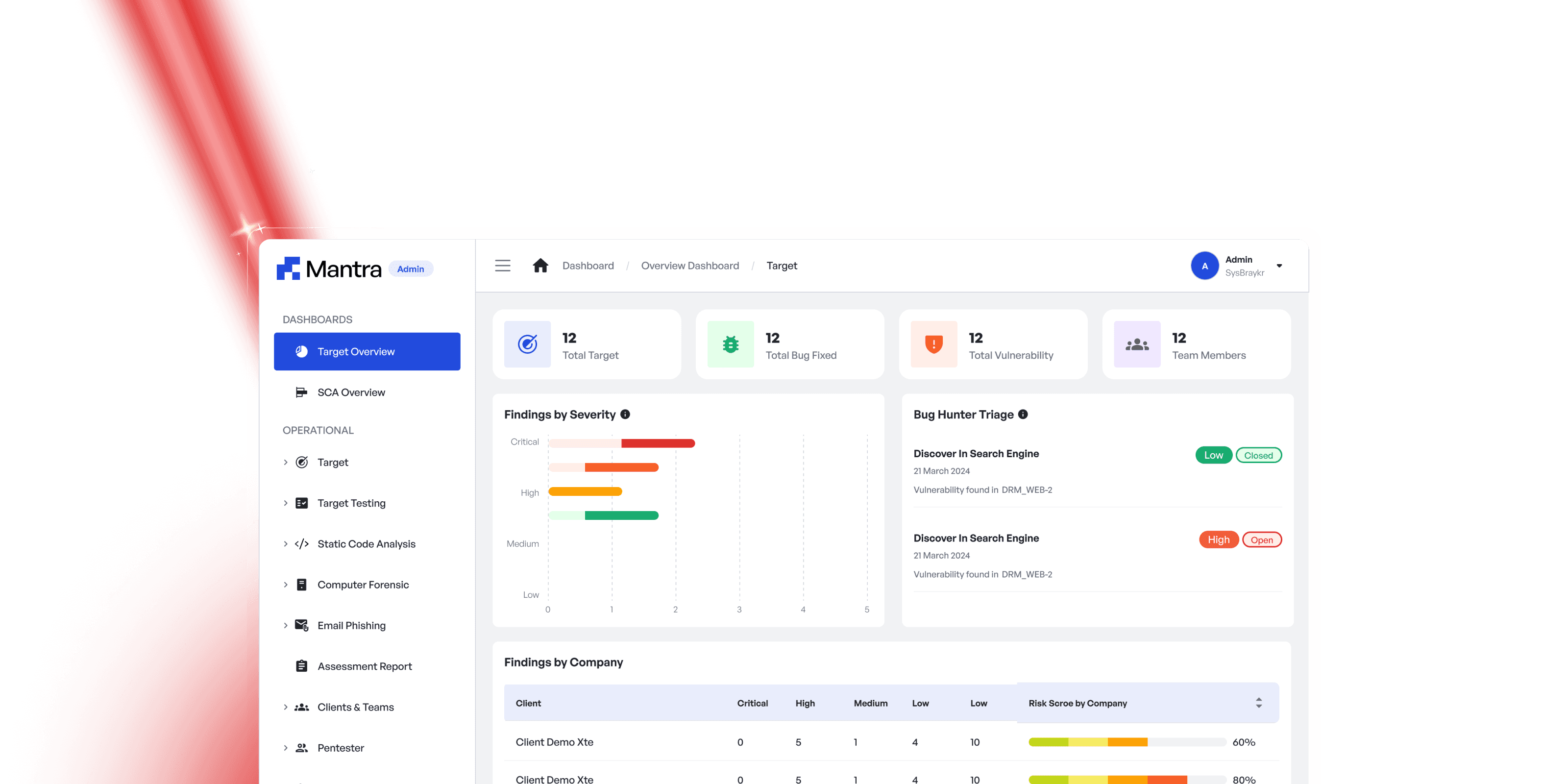
Hacking As a Service (HaaS) using Mantra is a full-cycle solution from SysBraykr designed to provide a holistic and comprehensive approach to your security needs. This service goes beyond technical testing, incorporating assessments of human and process factors to cover all these critical aspects. Our processes involve evaluating and improving security procedures while implementing best practices for risk mitigation. We deploy advanced tools and techniques to identify and address vulnerabilities. Through this comprehensive approach, we ensure your company’s security is not only robust but also adaptive to the constantly changing cyber threat landscape.
Hacking As a Service (HaaS) using Mantra is a full-cycle solution from SysBraykr designed to provide a holistic and comprehensive approach to your security needs. This service goes beyond technical testing, incorporating assessments of human and process factors to cover all these critical aspects. Our processes involve evaluating and improving security procedures while implementing best practices for risk mitigation. We deploy advanced tools and techniques to identify and address vulnerabilities. Through this comprehensive approach, we ensure your company’s security is not only robust but also adaptive to the constantly changing cyber threat landscape.
Hacking As a Service (HaaS) using Mantra is a full-cycle solution from SysBraykr designed to provide a holistic and comprehensive approach to your security needs. This service goes beyond technical testing, incorporating assessments of human and process factors to cover all these critical aspects. Our processes involve evaluating and improving security procedures while implementing best practices for risk mitigation. We deploy advanced tools and techniques to identify and address vulnerabilities. Through this comprehensive approach, we ensure your company’s security is not only robust but also adaptive to the constantly changing cyber threat landscape.
FEATURES
FEATURES
FEATURES
FEATURES
Features at a glance
Features at a glance
Features at a glance
We implement best practices for risk mitigation, and utilize advanced tools to identify and address vulnerabilities within your business using Risk-Based and Holistic testing processes. We use the Human-Process-Technology methodology to address both human and technical factors. Through this comprehensive approach, we ensure your company’s security is not only robust but also adaptive to the constantly evolving cyber threat landscape.
We implement best practices for risk mitigation, and utilize advanced tools to identify and address vulnerabilities within your business using Risk-Based and Holistic testing processes. We use the Human-Process-Technology methodology to address both human and technical factors. Through this comprehensive approach, we ensure your company’s security is not only robust but also adaptive to the constantly evolving cyber threat landscape.
We implement best practices for risk mitigation, and utilize advanced tools to identify and address vulnerabilities within your business using Risk-Based and Holistic testing processes. We use the Human-Process-Technology methodology to address both human and technical factors. Through this comprehensive approach, we ensure your company’s security is not only robust but also adaptive to the constantly evolving cyber threat landscape.
We implement best practices for risk mitigation, and utilize advanced tools to identify and address vulnerabilities within your business using Risk-Based and Holistic testing processes. We use the Human-Process-Technology methodology to address both human and technical factors. Through this comprehensive approach, we ensure your company’s security is not only robust but also adaptive to the constantly evolving cyber threat landscape.
Red-Teaming
Red-Teaming
Red-Teaming
Red-Teaming
Simulating on-site real-world attacks to test humans, process, and technology vectors.
Simulating on-site real-world attacks to test humans, process, and technology vectors.
Simulating on-site real-world attacks to test humans, process, and technology vectors.
Simulating on-site real-world attacks to test humans, process, and technology vectors.
VAPT
VAPT
VAPT
VAPT
Finding vulnerabilities across systems, following industry standards and prioritizing risks based on impact.
Finding vulnerabilities across systems, following industry standards and prioritizing risks based on impact.
Finding vulnerabilities across systems, following industry standards and prioritizing risks based on impact.
Finding vulnerabilities across systems, following industry standards and prioritizing risks based on impact.
Secure Code Analysis
Secure Code Analysis
Secure Code Analysis
Secure Code Analysis
Identify critical security flaws in source code and binaries before deploying your applications.
Identify critical security flaws in source code and binaries before deploying your applications.
Identify critical security flaws in source code and binaries before deploying your applications.
Identify critical security flaws in source code and binaries before deploying your applications.
Digital Forensics
Digital Forensics
Digital Forensics
Digital Forensics
Investigate and analyzes electronic evidence in security incidents to identify breaches and suspicious activities.
Investigate and analyzes electronic evidence in security incidents to identify breaches and suspicious activities.
Investigate and analyzes electronic evidence in security incidents to identify breaches and suspicious activities.
Investigate and analyzes electronic evidence in security incidents to identify breaches and suspicious activities.
Phishing
Phishing
Phishing
Phishing
Phishing simulations to measure and identify your teams readiness.
Phishing simulations to measure and identify your teams readiness.
Phishing simulations to measure and identify your teams readiness.
Phishing simulations to measure and identify your teams readiness.
Security Awareness
Security Awareness
Security Awareness
Security Awareness
Enhance your team's understanding of common attack methods and their potential impact.
Enhance your team's understanding of common attack methods and their potential impact.
Enhance your team's understanding of common attack methods and their potential impact.
Enhance your team's understanding of common attack methods and their potential impact.
Take Control of Your Security with Hacking As a Service
Take Control of Your Security with Hacking As a Service
Take Control of Your Security with Hacking As a Service
Take Control of Your Security with Hacking As a Service


Our Services
Company
Resources
© 2024 SysBraykr
Our Services
Company
Resources
© 2024 SysBraykr
Our Services
Company
Resources
© 2024 SysBraykr